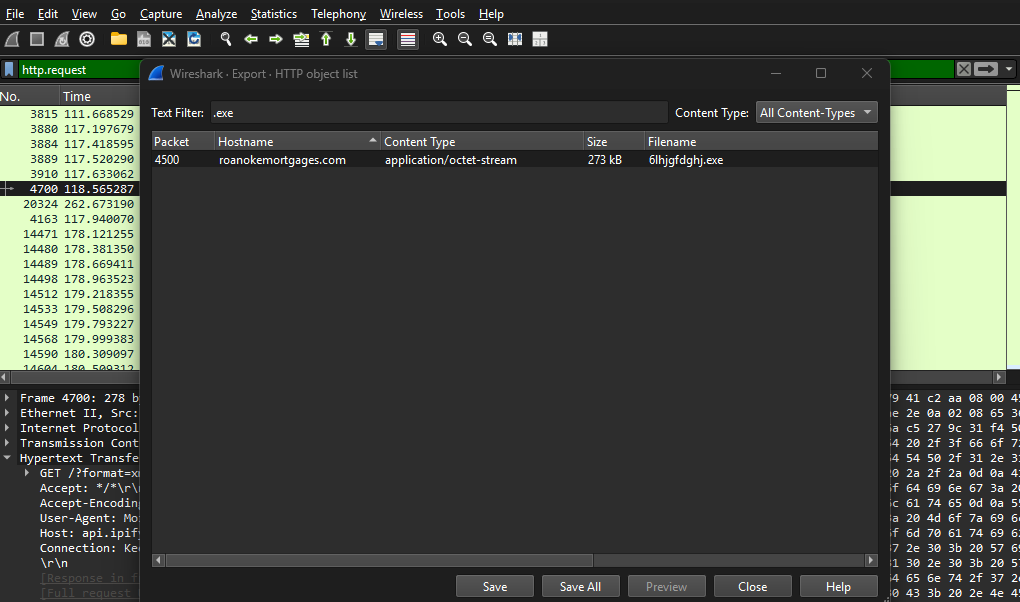
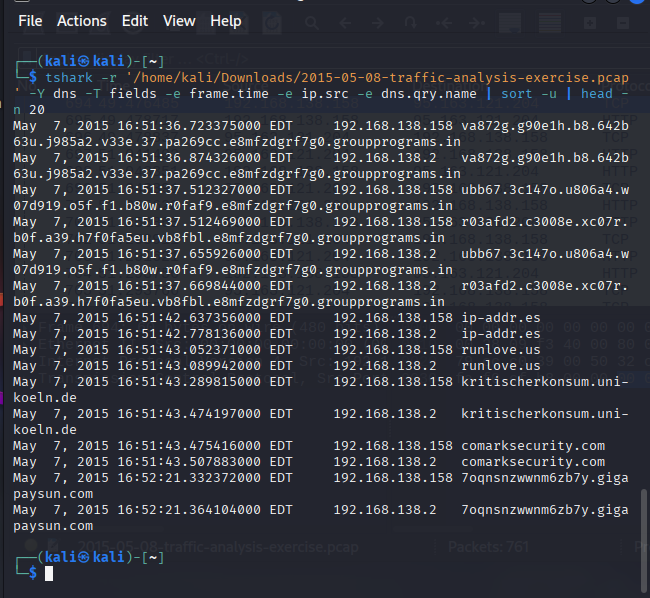
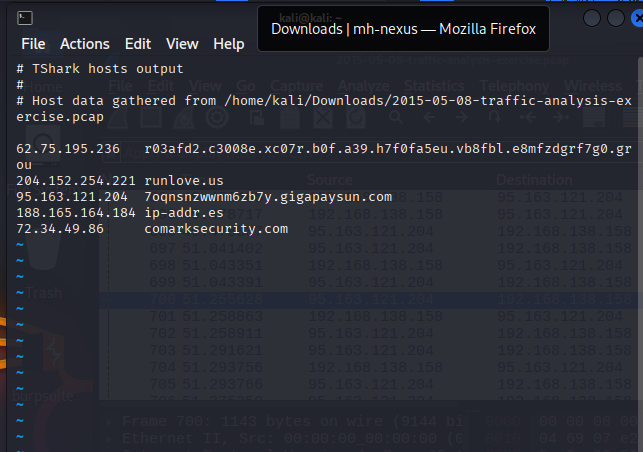
Find the Culprit — Malware Network Traffic Analysis
Analyzed a PCAP in Wireshark/TShark to track a Windows host infected by malware. Identified suspicious DNS and HTTP beacons, traced C2 domains, and confirmed Trojan/backdoor activity. Delivered a structured incident report with IOCs, timeline, and containment recommendations including stricter egress filtering and DNS monitoring.
